Purple teaming is the incorporation of both offensive red team and defensive blue team practices into a continuous evidence-based security validation program. Instead of adversarial evaluation, purple teaming is a cooperative approach, in which the two teams collaborate openly to test, tune, and validate detection and response functions to real-world attacker approach techniques. The strategy reinvents itself as a series of improvement cycles so that a single penetration test could be an improvement cycle that measurably enhances the defenses of the organization.
The Characteristics of Modern Purple Teaming
Purple teaming has three key principles that set it apart from red or blue team work. Initially, it focuses on transparency instead of stealth. The red team attack methods are practiced, which allows the defenders to observe the attack and change tuning in real-time. Second, it emphasizes validation over discovery, which means that it is not only necessary to find vulnerabilities. But it is also necessary to ensure that the implemented detections are effective. Third, it is persistent in its iteration; teams repeat attack, detect, fix, and retest the loop till the defensive coverage can be confirmed to be effective.
The purple teaming role can be implemented as a special facilitation position or as a process of cooperation of the red and blue teams that already exist. The important thing is the systematic coordination: a realistic attack scenario should be defined, based on the intelligence on threats, and then implemented step by step with the defenders observing, finding openings in the visibility or response, making improvements, and immediately retesting it to confirm it is working.
Top 20 TTPs in Existing Purple Teaming Exercises
Purple teaming exercises put more emphasis on techniques that mirror the present state of the threat, including TTPs that have been detected in previous ransomware operations, nation-state activity, and commodity malware. In the coherence of 2024-2025 threat intelligence reports, the set of techniques used is concentrated and contributes to the overwhelming majority of successful attacks.
Initial Access
T1566: Phishing is the most common entry point, and spearphishing attachments (T1566.001), links (T1566.002), and service-based phishing (T1566.003) are the initial access points of the majority of enterprise breaches. The purple teaming exercises are an evaluation of the defensive stack as a whole. It includes email gateways, sandboxing, user awareness, endpoint detection of malicious Office macros, and incident response processes. In addition, current EDR systems have more than 115 phishing variant detection rules, but organizations continue to fail to identify advanced lures that avoid the use of static signatures.
T1078: Valid accounts have since risen as the credential-based attacks grew by 42% between 2024 and 2025. As the number of stolen credentials in circulation due to infostealer malware goes above 1.7 billion, those who break the technical controls are starting to go around by simply using legitimate credentials. Purple teaming exercises test the capability of organizations to identify impossible travel, strange access patterns, and privilege escalation with stolen credentials.
Execution
T1059: Command and Scripting Interpreter is present in 93% of malware samples studied in 2025, which is the second most common technique of all tactics. The malicious code is also executed using PowerShell, cmd.exe, bash, Python, and other native interpreters by adversaries without leaving traditional executables. The purple teams are used to investigate whether defenders are capable of differentiating between malicious and legitimate administrative activity by command-line logging, script block logging, behavioral analysis, and identification of obfuscated or coded commands.
T1204: User Execution is the next step that complements phishing, by testing to verify the last step: Will the user click, and will endpoint controls prevent the user? Purple teams confirm that security awareness training is reflected in lower risk. In addition, the technical controls offer defense in depth in the event of a failure on the part of users, with 148 rules invented around this technique.
Persistence
T1053: Scheduled Task/Job is the seventh most common ATT&CK method, which enemies employ to have continuing access by using legitimate task-scheduling tools. Attackers use schtasks.exe and at.exe on Windows, cron jobs, and systemd timers on Linux. Purple team exercises challenge the ability of defenders to identify the presence of suspicious task creation and identify task execution that operates along an unusual path or with high privileges. It also includes the reaction to the challenge before recurring malicious execution.
Privilege Escalation
T1055: Process Injection became the most popular technique in 2025, and it was found in 93% of examined malware malicious campaigns. The attackers introduce bad code into the clean processes to avoid detection, raise privileges, and access process memory. At this time, the purple teams demonstrate that EDR solutions can identify the injection methods of DLL injection, process hollowing, thread execution hijacking, and reflective loading. These are the methods that overcome conventional antivirus solutions.
Defense Evasion
T1027: Obfuscated Files or Information enables adversaries to evade detection by signature-based and/or static analysis with the aid of encoding, encryption, packing, steganography, and polymorphic code generation. Purple teams are used to test sandbox detonation, behavioral scanning, memory scanning, and the detection of the presence of obfuscation. Moreover, it includes high entropy files, suspicious packing, and anti-analysis.
T1070: Indicator Removal T1070.001: Removal of event logs T1070.004: Deletion of files T1070.005: Removal of network share connections T1070.006: Timestomping. Purple teams confirm that the forwarding of logs to centralized SIEM is near real-time, that the critical logs are tampered with, and that clearing or modifying logs raises an immediate alert.
T1562: Impair Defenses were the most common defense evasion tool in 2025, with enemies always disabling Windows Defender, EDR agents, firewalls, and logging services before executing the payloads. In addition, Purple tests are used to verify the presence of self-protection in security tools, the presence of service stop attempt alerts, and endpoint agents resisting termination by malicious processes.
T1218: Signed Binary Proxy Execution is taking advantage of trusted, Microsoft-signed binaries, also known as living-off-the-land binaries (LOLBins), in order to execute malicious code without being caught by application whitelisting and signature validation. These methods are regsvr32.exe, rundll32.exe, mshta.exe, and cmstp.exe. Purple teams prove the detection of any suspicious parent-child process relationships, command-line anomalies, and network connections initiated by administrative utilities.
Credential Access
T1003: OS Credential Dumping is the third most prevalent technique and an attack chain of critical escalation. The credentials of LSASS memory (T1003.001), Security Account Manager (T1003.002), and NTDS.dit database of Active Directory are dumped by adversaries to facilitate the lateral movement and compromise of the domain (T1003.003) later. Moreover, Purple teams challenge LSASS protection controls (Credential Guard, PPL), honey tokens deployed in credential stores, as well as behavioral representation of tools such as Mimikatz, ProcDump, and custom dumpers.
Discovery
T1082: System Information Discovery is positioned seventh on the top ten techniques list because the adversaries will list operating system version, hardware specification, installed software, and system architecture in order to optimize further exploitation and evasion. Since this method is based on valid system tools (systeminfo.exe, uname, wmic). Purple Teams determines whether the defenders can identify abnormal discovery behavior by using process relationships, quantity of enumeration orders, and relating to other suspicious discovery events.
T1083: File and Directory Discovery and T1069: Permission Groups Discovery are reconnaissance tools that come before the exfiltration of the data and the further spreading of it. Additionally, Purple exercises confirm the alerts of Security Information and Event Management (SIEM) detects atypical volume of directory enumeration, attempts to view sensitive file shares, or the process of enumerating privileged groups in Active Directory.
Lateral Movement
T1021: Remote Services is the major lateral movement vehicle, and the ransomware campaigns have highly utilized either RDP (T1021.001) or SMB/Windows Admin Shares (T1021.002). All of the considered major ransomware families in 2024, including Fog, RansomHub, BlackBasta, and LockBit, used remote services as the propagation tool. Moreover, Purple teams verify segmentation of the network, Pass-the-Hash authentication discovery, track record of use of privileged accounts in more than one system, and bastion host controls.
T1570: Lateral Tool Transfer allows attackers to spread malware, credential dumpers, and post-exploitation frameworks in the environment using SMB shares, FTP, or cloud storage services. At the same time, purple exercises are put in place to monitor file integrity checks on crucial systems, file transfer detection over the network, and correlation of the tool distribution with the following malicious execution.
Command and Control
T1071: Application Layer Protocol was one of the most prevalent techniques in 2025 because the attacker will insert C2 traffic as regular HTTP/HTTPS web traffic to avoid being detected by the network. Purple tests determine whether the proxy and firewall rules prevent the usage of known C2 domains. Whether the inspection of the use of the SSL/TLS reveals malicious payloads, and whether the behavioral analytics identify beaconing patterns of the use of the C2 communication.
T1090: The T1090.001 is based on proxy techniques, which enable adversaries to pivot on compromised systems and also hide the actual origin of the command-and-control traffic (T1090). Purple exercises confirm egress monitoring, unusual proxy configuration detection, and identification of systems that all of a sudden start transferring large amounts of traffic.
T1105 Ingress Tool Transfer: Adversaries who have been initially compromised may download more malware, dump credentials, or use additional tools of lateral movement. Purple teams are used to determine whether the downloads through known malicious infrastructure are prevented by a web proxy. Whether the downloaded executable is detonated by a sandbox, and whether the downloaded tools are prevented from executing by endpoint controls.
Impact
T1486: Data Encrypted for Impact is the final form of ransomware attacks and the most lucrative form of impact method. Any successful ransomware execution starts with prior phases of initial access, subsequent lateral mobility, and appropriation of credentials, yet it leads to encryption. Moreover, purple exercises are used to test the backup and recovery processes, detecting an unusual file modification behavior, honeypot files that send an immediate alert in case of encrypted files, and the capability to isolate the impacted systems before full encryptions have taken place across the entire enterprise.
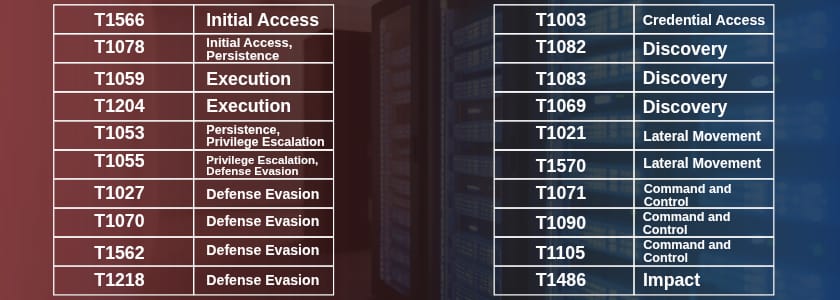
Summary Table: Top 20 Purple Team TTPs
| Rank | Technique ID | Technique Name | Tactic | Prevalence / Priority |
| 1 | T1566 | Phishing | Initial Access | Most common initial access |
| 2 | T1078 | Valid Accounts | Initial Access, Persistence | 42% increase, 1.7B stolen creds |
| 3 | T1059 | Command and Scripting Interpreter | Execution | 93% of malware |
| 4 | T1204 | User Execution | Execution | 148 detection rules |
| 5 | T1053 | Scheduled Task/Job | Persistence, Privilege Escalation | 7th most prevalent |
| 6 | T1055 | Process Injection | Privilege Escalation, Defense Evasion | Most prevalent in 2025 |
| 7 | T1027 | Obfuscated Files or Information | Defense Evasion | Critical evasion technique |
| 8 | T1070 | Indicator Removal | Defense Evasion | Anti-forensics |
| 9 | T1562 | Impair Defenses | Defense Evasion | Top defense evasion 2025 |
| 10 | T1218 | Signed Binary Proxy Execution | Defense Evasion | LOLBins abuse |
| 11 | T1003 | OS Credential Dumping | Credential Access | 3rd most common |
| 12 | T1082 | System Information Discovery | Discovery | 7th in top 10 |
| 13 | T1083 | File and Directory Discovery | Discovery | Pre-exfiltration |
| 14 | T1069 | Permission Groups Discovery | Discovery | AD enumeration |
| 15 | T1021 | Remote Services | Lateral Movement | All ransomware families |
| 16 | T1570 | Lateral Tool Transfer | Lateral Movement | Malware distribution |
| 17 | T1071 | Application Layer Protocol | Command and Control | 4th most common |
| 18 | T1090 | Proxy | Command and Control | Traffic obfuscation |
| 19 | T1105 | Ingress Tool Transfer | Command and Control | Tool download |
| 20 | T1486 | Data Encrypted for Impact | Impact | Ransomware |




