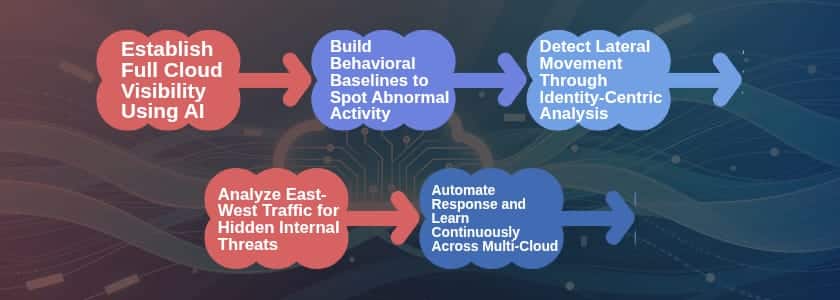
Cloud environments provide organizations with speed, flexibility, and scale. Nonetheless, attackers exploit the same flexibility, as well. When they violate one of the workloads, they do not usually quit. Rather, they just slide around stealing other systems, identities, and data. The common security tools fail to detect lateral movement, which is usually normal. Attackers employ credentials, trusted services, and legitimate tools. Consequently, rule-based systems lack the threat until they have already been damaged.
AI transforms this to the opposite. Artificial intelligence reveals hidden patterns of behavior and predicts massive amounts of activity in real time by observing behavior patterns and analyzing them, which human analysts and stationary tools do not. Thus, organizations today look up to AI to seal this risky visibility gap.
How AI Helps Detect Lateral Movement in Cloud Environments at an Early Stage
The article How AI Helps Detect Lateral Movement in Cloud Environments begins with the visibility. AI systems will examine cloud logs, identity events, API calls, and network traffic within accounts and regions in an endless manner. AI can link events into meaningful sequences, as opposed to responding to single events. Consequently, security teams observe the entire attack path, and not fragmented indications.
Attackers generally operate laterally when they have gained initial access. They scan the internal resources, reuse the identities, escalate privileges, and pivot between the workloads. AI models identify such models since they first identify normal behavior. As soon as a user account enters unknown services, new areas, or confidential resources, AI sounds an alarm. Defenders therefore prevent attackers until they access important assets.
Identity-Centric Detection in Cloud Environments
Attackers also make use of compromised identities extensively to detect Lateral Movements. They steal tokens, mishandle permissions, and take advantage of misconfigurations. Identity is central to the detection by AI. It follows the behaviour of identities over services, accounts, and geographies.
AI is instantly responsive when an identity is abruptly broadening its accessibility. It identifies privilege scaling, suspicious role pretences, and abnormal usage of APIs. As a result, teams are able to revoke access before the proliferation of attackers.
This identity-based strategy is important since cloud attacks do not often remain limited to one host. Rather, identities are the primary weapon of attackers in jumping between services. AI counters such an advantage.
Network and East-West Traffic Analysis
The east-west traffic occurs within the cloud condaccount, and it is through this that lateral movement occurs. Traditional perimeter tools do not take internal communication into account. The analysis of traffic patterns carries out transformations in AI among workloads.
AI detects suspicious attempts to connect, unsolicited data transfer, and anomalous service communication. An example is when a compute instance makes an unexpected call to the database it had not previously communicated to, AI sends a warning. Hence, defenders detect lateral movement without malware signatures.
It is particularly useful when there are many microservices in the architecture and thousands of services involved in communication all the time. AI differentiates between regular and malicious exploration of the service.
Automation and Faster Incident Response
Detection does not prevent lateral movement. Speed matters. Artificial intelligence combines the methods of detection and automated responses. In the case of suspicious lateral movement, AI, in turn, activates containment.
As an example, AI can separate the workloads, credential rotation, or block questionable network paths automatically. Consequently, the attackers slowed down. The security teams investigate the context rather than scrambling to investigate the issue afterwards.
Automation can also minimize bornout. Analysts would not have to answer all alerts manually. AI deals with routine containment, and human beings deal with strategic decisions.
How AI Helps Detect Lateral Movement in Cloud Environments Across Multi-Cloud Setups
A large number of organizations have numerous cloud providers. It is this complexity that introduces blind spots, which the attackers use. How AI can be used to identify lateral movement in cloud environments is even better in multi-cloud environments.
One of the applications of AI platforms is to bring together the telemetry of multiple providers into one behavioral model. They identify lateral movement across accounts, clouds, and services. Thus, attackers will not be able to conceal themselves by hopping onto platforms.
This single sight also eases security activities. The teams would have uniform detection logic rather than administering tools on a per-cloud basis.
Continuous Learning Against Evolving Threats
Attackers are constantly evolving and altering methods in order to overcome defenses. The tools that are static lag behind very fast. AI, in its turn, is self-educated with every new piece of information. It evolves the models of detection with the change of attackers.
When attackers are engaging in new lateral movement methods, AI monitors the behavior and renews baselines. With time, it can detect without human creation of rules. Thus, organizations remain ahead and do not respond late. This is an ongoing learning ability that renders AI indispensable towards cloud security resilience over the long term.
How AI Helps Detect Lateral Movement in Cloud Environments for Modern Enterprises
Contemporary businesses are not allowed to be supported solely with perimeter defenses. Cloud security requires smartness, speed, and flexibility. The future of successful defense is defined in How AI Helps Detect Lateral Movement in Cloud Environments.
AI observes the attempts made by attackers. It links signals, cognizes intent, and acts immediately. Thus, companies secure sensitive resources even when the cloud environment is one that is highly dynamic.
With the rise in the rate of cloud adoption, AI becomes a luxury of the past. Businesses that integrate AI-based detection remain resilient. The ones who procrastinate are the ones who are vulnerable.
Conclusion
AI also changes cloud security by revealing the horizontal movement that cannot be observed by traditional tools. It connects behavior and identities with internal traffic in real time and finds the obscure attack routes at an early stage. Consequently, the organizations prevent threats before attackers access important data. AI also responds faster by automating, which minimizes damage and decreases the workload of the analysts.
Frequently Asked Questions
1. Why does lateral movement pose such a serious risk in cloud environments?
Lateral movement enables the attackers to increase access once they have been compromised. They crawl carelessly to sensitive systems without raising the classical warnings. Thus, organizations tend to see violations when it is too late.
2. Can AI completely replace human security analysts?
AI does not replace humans. Rather, it increases their performance. AI works on the scale, speed, and pattern recognition, and analysts work on the investigation and strategy.
3. Is AI-based detection suitable for small and mid-sized organizations?
Yes, AI is easily scalable and minimizes the number of people. Smaller teams will also gain, as AI will not need large security personnel to detect and respond, since it will automate the process.





