Understanding Vulnerability Assessment and Penetration Testing (VAPT)
Understanding Vulnerability Assessment and Penetration Testing is very important. Imagine your company’s computer system is like your house. You want to feel safe and secure, right? But what if there are cracks in the walls or a loose lock on the door? Hackers, the bad guys of the internet, are always looking for ways to sneak in and steal your stuff, just like valuable data from your company.
VAPT, which stands for Vulnerability Assessment and Penetration Testing, is like having a security expert come and check your whole house. They’ll find those weak spots, like the cracks and loose locks, and tell you how to fix them before anyone tries to break in. This helps companies all over the world, especially here in the Middle East, keep their information safe from cyberattacks. Data breaches are scary, but VAPT helps companies find those hidden dangers before they become a big problem.

Why Security Matters: Keeping the Bad Guys Out
Businesses are bombarded with cyberattacks these days- malware, phishing, ransomware, the whole nasty bunch. This makes it tough to keep their digital stuff safe, especially in the Middle East where everyone’s going digital. The good news? VAPT helps companies fight back and stay secure!
Enter VAPT—Vulnerability Assessment and Penetration Testing by IT Butler. It can be your knight in shining armor, a beacon of hope, and the defender of your IT assets and system’s vulnerabilities.
Vulnerability Assessment (VA)
Vulnerability Assessment (VA) is the first step of VAPT, finding weaknesses in a company’s systems, networks, and apps. It checks for problems like old software or bad setups using tools and hands-on methods. This helps businesses find where hackers could get in before they do.
Penetration Testing (PT)
Penetration Testing (PT) goes beyond VA by pretending to be real hackers to test how well security measures work. Ethical hackers, called “white-hat” hackers, try to break into systems and data through known weaknesses. This helps organizations understand their security strengths and decide what to fix first.
Vulnerability and Penetration Testing – Together – They are More Powerful
Together, Vulnerability Assessment and Penetration Testing form a formidable alliance – a dynamic duo that leaves no stone unturned in the quest for cyber resilience. But why are they indispensable for companies in the GCC and MENA region?
Two Sides of a Coin
Vulnerability Assessment and Penetration Testing are two interrelated but distinct approaches to assessing and enhancing cybersecurity. Vulnerability Assessment thoroughly identifies and prioritizes system, network, or application vulnerabilities. On the other hand, Penetration Testing involves simulating real-world cyber-attacks to exploit vulnerabilities and assess the effectiveness of security measures.
About VAPT and the GCC and MENA Region
Vulnerability Assessment and Penetration Testing. Now WHY is VAPT, not just an option but a necessity for companies in the GCC and MENA region?
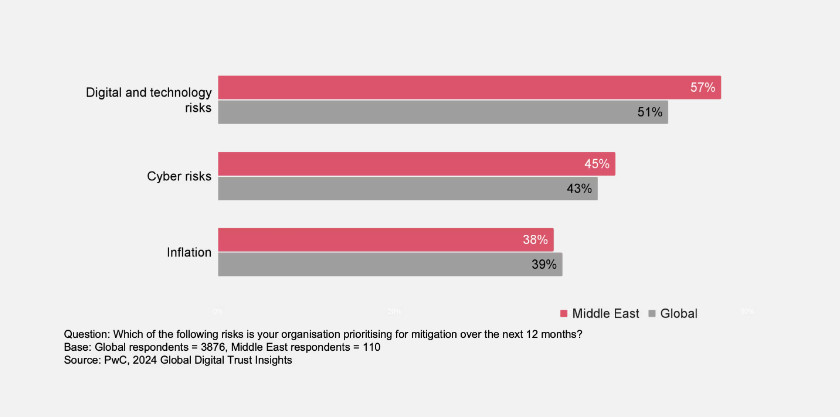
With its rapid digitization, the booming GCC and MENA region faces a hidden adversary – cybercrime. Over half (53%) of companies in Saudi Arabia and the Middle East are concerned about attacks, and the construction sector is especially vulnerable, with 75% of executives feeling exposed. VAPT emerges as a critical defense mechanism, simulating cyberattacks to identify and fix security weaknesses before exploiting them. By proactively uncovering vulnerabilities, prioritizing risks, and ensuring compliance, VAPT empowers businesses in the GCC and MENA region to stay ahead of cyber threats in today’s digital landscape.
Source: PwC Digital Trust Insights 2024: Middle East findings
Why Do Companies Need Vulnerability Assessment and Penetration Testing
The GCC and MENA region is a hotbed for cybercrime, with no industry safe from attack. Countries like Saudi Arabia, UAE, Bahrain, and Qatar are experiencing rapid growth because of which from financial institutions to healthcare providers, businesses are facing constant threats of data breaches and disruption.
However, there’s a solution: Vulnerability Assessment and Penetration Testing (VAPT). VAPT acts as a beacon of hope in this digital landscape, proactively identifying security weaknesses before attackers can exploit them. By addressing these vulnerabilities, businesses can bolster their defenses, mitigate risks, and safeguard their valuable assets.
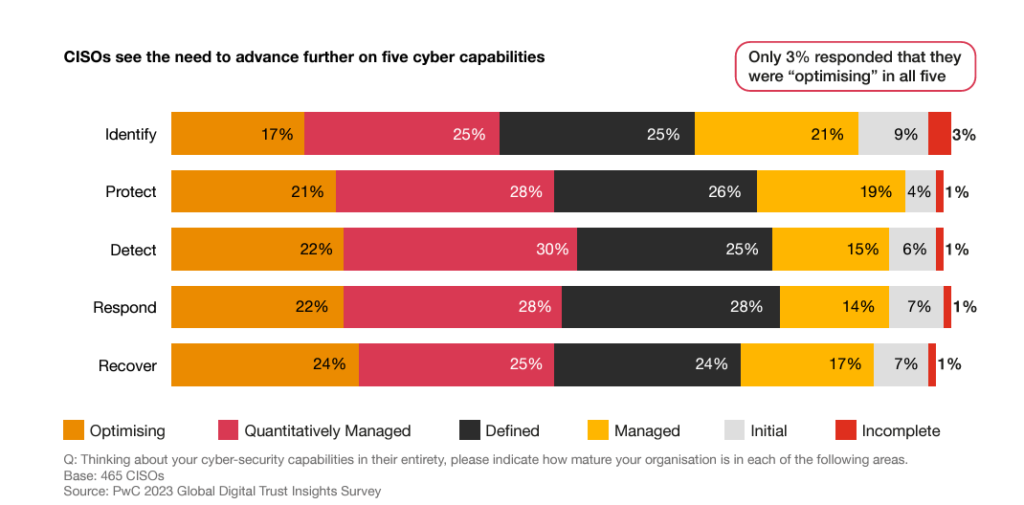
Test Your Company’s Cyber Strength: Evaluate your organization’s cybersecurity posture with this handy chart outlining five key capabilities. See where you excel and identify areas for improvement!
The importance of VAPT in the GCC and MENA region goes far beyond just meeting compliance requirements. In this digital age, trust is paramount. Customers, partners, and stakeholders increasingly value businesses that prioritize cybersecurity. Regular VAPT assessments, conducted by a trusted provider like IT Butler, demonstrate a proactive commitment to data security and overall business resilience. IT Butler’s VAPT services are specifically tailored to address the unique threats faced by companies in the GCC and MENA region. By partnering with IT Butler for VAPT, you send a clear message – your business is built on a foundation of trust and unwavering security.
Let’s look into a few steps in Performing a VAPT Test:
1. Vulnerability and Penetration Testing – Define the Scope:
This entails determining the networks, systems, and applications that will be tested and any constraints or limitations. If the scope is well specified, the testing team can concentrate on the most important assets and vulnerabilities.
2. Reconnaissance:
Data on the target environment, such as IP addresses and domain names, is collected during reconnaissance. This phase aids in comprehending the organization’s digital presence and possible vulnerabilities.
3. Vulnerability Scanning:
The testing team utilizes specialized tools to automate scans, pinpointing known vulnerabilities in the target system, such as outdated software or misconfigurations. Prioritizing critical issues, they analyze the results for swift resolution.
4. VAPT – Manual Testing:
Although automated tools can detect numerous vulnerabilities, manual testing remains crucial for revealing intricate or nuanced issues that automated scans may overlook. Skilled penetration testers mimic real-world attacks, striving to exploit vulnerabilities and obtain unauthorized system access.
5. Analysis and Reporting:
The testing team evaluates results from automated scans and manual tests, creating a detailed report with identified vulnerabilities, their severity, and recommended fixes. Clear, concise reporting is crucial for organizations to grasp risks and respond effectively.
6. Remediation:
After the VAPT test reveals vulnerabilities, organizations take action to fix them, which can include applying patches, adjusting settings, or enhancing security measures to reduce risks.
7. Validation Testing:
Validation testing is essential post-remediation to confirm effective vulnerability addressing. It ensures robust security measures and significantly lowers the risk of exploitation.
8. Documentation and Continuous Improvement for Vulnerability Assessment and Penetration Testing
Thorough documentation is essential for VAPT. It captures testing methods, results, and solutions, aiding in maintaining an audit trail and enhancing security practices. VAPT is continuous and must adapt to evolving cyber threats.
Vulnerability Assessment and Penetration Testing – Food for Thought
Unfortunately, it is a sad truth that despite VAPT’s clear benefits, many companies in the GCC and MENA region remain hesitant to embrace this transformative approach to cybersecurity. Some cite budgetary constraints, while others fear the complexity of implementation. But inaction is not an option in the face of an ever-evolving threat landscape.
The Bold takes the Leap
The rewards for companies willing to leap are immeasurable. By investing in VAPT, businesses in the GCC and the MENA region can unlock a world of opportunities, empower their teams, and confidently embark on a journey of digital transformation.
Raising the Sword against Cyber Attacks for Now and EVER
So, let us raise our swords and shields high and embark on this epic quest for cyber resilience. Together with IT Butler, we can conquer the darkness, vanquish our foes, and emerge victorious in the battle for digital supremacy. The time for action is now – the fate of our digital resilience and future hangs in the balance.
Vulnerability Assessment and Penetration Testing – Conclusion
In conclusion, Vulnerability Assessment and Penetration Testing (VAPT) stand as indispensable pillars in safeguarding businesses against the ever-evolving landscape of cybersecurity threats. As digitalization accelerates across industries in the GCC countries, the importance of proactive security measures like VAPT cannot be overstated. By identifying and remedying vulnerabilities before they can be exploited by malicious actors, businesses can fortify their defenses, protect critical assets, and uphold regulatory compliance. Moreover, investing in VAPT reflects a commitment to ensuring trust and confidence among customers and stakeholders, essential elements for sustained success in today’s interconnected world. As GCC businesses navigate the complexities of the digital age, integrating VAPT into their cybersecurity strategy emerges not just as a necessity but as a strategic imperative for resilience, innovation, and growth in the face of evolving cyber threats.
